Shiba Inu core developer Kaal Dhairya has issued an in depth safety replace following the September 12 incident that exploited validator signing energy on the Shibarium PoS bridge to push a malicious state/exit and withdraw a number of belongings. The put up, revealed on September 21, 2025 outlines what occurred, what has been performed up to now, and what’s going to govern a phased restoration as soon as impartial opinions conclude.
Shiba Inu Core Dev Shares Another Update
In a private foreword that framed each the technical and human dimensions of the episode, Dhairya opened by distancing himself from any singular management mantle and reiterated the unique ethos driving his work. “I need to make clear first: I’m not ‘the lead.’ I by no means was and by no means need to be. I’m only a builder who guess on SHIB’s ethos,” he wrote, including that “in moments like these, you understand you’ll have simply been a pawn in the entire recreation.”
The Shiba Inu core dev cautioned that, given “the sophistication of this assault,” he couldn’t presently vouch for the security of any present keys, and he signaled fatigue with expectations that particular person contributors might “hold all of it collectively” with out broader structural help.
The account of the incident describes how, at 18:44 UTC on September 12, “unauthorized validator signing energy was used to push a malicious state/exit by way of the PoS bridge.” The methodology, per the replace, mixed short-lived stake amplification with malicious checkpoint/exit proofs to authorize withdrawals. Post-incident on-chain exercise linked to the attacker is claimed to incorporate gross sales of parts of ETH, SHIB and ROAR, although the crew is withholding the “evolving pockets graph” whereas containment and coordination with authorities proceed. “We’ll launch the complete technical narrative after doing so not will increase danger,” the put up states.
Immediate measures embrace limiting particular bridge operations to forestall new unauthorized exits, upgrading and gating contract pathways overlaying deposits, withdrawals, claims and rewards, and making use of “focused defensive controls towards misuse of delegated stake.” The crew says it recovered and secured at-risk BONE on the stake-manager degree and notes that any short-term BONE stake beneath the attacker stays “successfully immobilized” by interventions and protocol mechanics.
Key and custody hygiene steps have concerned rotating validator signers and migrating contract management to multi-party {hardware} custody, whereas stay monitoring and automatic alerts proceed in coordination with exchanges, exterior safety researchers, incident-response companies and related authorities.
The replace additionally engages ceaselessly requested questions on validator compromise and operational accountability. It says validator signing keys have been “primarily saved in AWS KMS, with uncommon utilization on developer machines,” and that final duty for key administration lies with operational management. While a single intrusion vector has not been confirmed, preliminary prospects embrace a developer machine compromise, a cloud KMS compromise, publicity throughout an AWS-to-GCP migration, or a supply-chain assault, resembling through npm.
The put up acknowledges decentralization shortcomings underscored by the truth that “10 of 12 validators” signed the malicious state, and it commits to larger validator decentralization, stronger key-rotation coverage, tighter custody, improved disclosures, and better due-diligence thresholds for delicate entry.
A roadmap preview units out 4 gated phases. “Containment” stays ongoing with restricted bridge performance and stay monitoring; “Hardening,” in collaboration with Hexens, contains signer/validator hygiene, policy-level controls resembling price limits, problem home windows and circuit-breakers, and deny-list extensions the place technically acceptable.
Next, “Safe Restoration” won’t start till impartial opinions log off on mitigations, post-incident integrity checks move and drills on take a look at environments succeed, with restoration executed in phases and with rollback levers; lastly, a complete technical postmortem will precede a community-reviewed remediation path for affected customers and liquidity, with the replace noting that “token-specific approaches might differ.”
Timelines stay deliberately unspecified: “We gained’t publish dates that might be gamed by an adversary,” the crew writes, reiterating that updates will put up to official channels.
For Shiba Inu token holders and victims, the message is blunt: watch out for scams, ignore unverified “restoration/declare portals,” and count on bridge restrictions to persist “till we verify it’s secure to revive.” Questions about bridging again to Ethereum, the timing of bridge resumption, validator rotation and full audit all obtain the identical reply—security first, particulars to comply with when safety permits. On fund restoration and potential compensation, the crew says choices are being evaluated and any proposal will probably be revealed for group overview “as soon as viable and safe.”
The Shiba Inu developer closes by reaffirming priorities and situating communication inside a disciplined cadence. “Our priorities are unchanged: defend customers, safe the community, include the attacker, and restore companies safely.” The subsequent main communication, he writes, would be the technical postmortem and a remediation proposal “as soon as the setting is secure for full disclosure.”
At press time, Shiba Inu traded at $0.00001207.
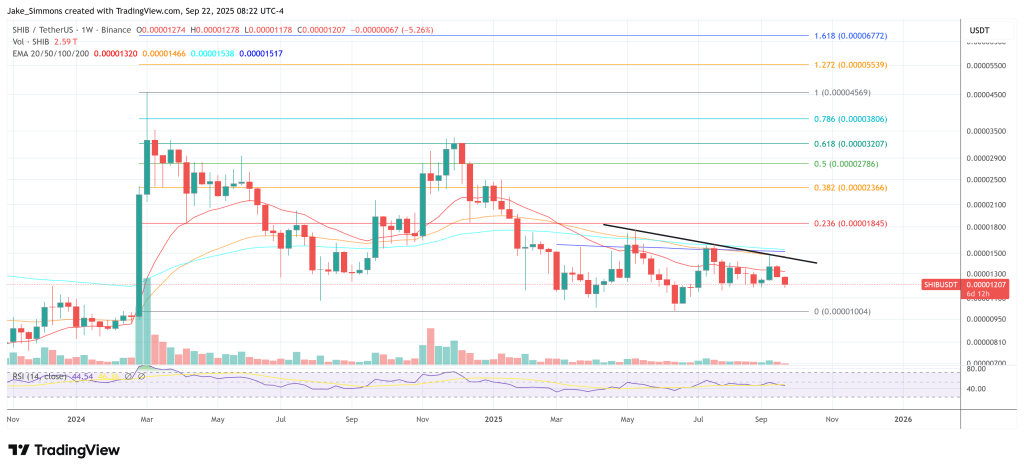
Featured picture created with DALL.E, chart from TradingView.com

Editorial Process for bitcoinist is centered on delivering totally researched, correct, and unbiased content material. We uphold strict sourcing requirements, and every web page undergoes diligent overview by our crew of high expertise consultants and seasoned editors. This course of ensures the integrity, relevance, and worth of our content material for our readers.